To Battle Account Takeover Attacks, Imperva ATO Enlists Automation, Machine Learning
Cybersecurity firm Imperva’s new account takeover protection leverages machine learning to better detect and stop account hijacking IDN explores Imperva Account Takeover (ATO) Protection with Imperva VP George McGregor.
by Vance McCarthy
Tags: ML, ATO, bots, cybersecurity, Imperva, mitigation,

vp product marketing

"We utilize machine learning to generate a mitigation strategy per attack. The detection certainty of an [ATO] attack depends on the accumulated information."
 Integration Powers Digital Transformation for APIs, Apps, Data & Cloud
Integration Powers Digital Transformation for APIs, Apps, Data & CloudCybersecurity firm Imperva is tackling account takeover protection with an offering that aims to detect and stop cyber attackers from using stolen credentials to hijack accounts.
Imperva’s ATO Protection uses a multi-layered, intent-based detection process to identify malicious logins. It aims to protect websites, business-critical APIs, legacy systems and enterprise and consumer apps that use open source software.
“Combating account takeover has especially been a priority for us because it is a primary use case for our customers, with it comprising a large percentage of the bot traffic we see, and because of its widespread impact,” Imperva’s vice president of product marketing George McGregor told IDN.
“When cybercriminals harvest stolen credentials and use automated botnets to test them and attempt to gain illegal access to resources, it consumes bandwidth, and, when the attackers are successful, it can have a devastating impact on the hacked business’ reputation,” he added.
McGregor noted that the profile for an ATO attack is continually changing, and attack tools are improving. In light of that, he said, the engineering of Imperva Account Takeover Protection aims to provide reliable protection, alongside adaptability.
To launch account takeover attacks, we know that cybercriminals have a more comprehensive array of tools at their disposal than ever before.
Attackers can launch volumetric bot floods or circumvent traditional security tools by staying under the radar with more complex low and slow attacks where they follow regular site login activity patterns and put forth a great deal of effort to keep their attack in line with regular login traffic, taking into account additional factors like activity patterns.
Attackers use anonymous proxies and IPs to distribute the attacks, which makes blocking by IP and geography actually less effective as the attacker can change IPs and geolocations in a matter of minutes.
Using automation tools, attackers can disguise themselves as legitimate web browsers, using headless browsers, mobile emulators with combination automation including AI emulating actual human behavior to disguise themselves as legitimate users.
With these attackers’ resources and tactics in mind, Imperva’s ATO solution has several layers which are engineered to work together to deliver rapid response, McGregor added.
Our mitigation is automatic based on intent-focused detection when it comes to protecting our customers from account takeover attempts.
We maintain a database of client applications, such as consumer applications (browsers, mobile applications), web services (monitoring services, scanners), development frameworks (curl, wget, php) and malicious clients (spammers, DDoS agents).
Each client behavior is monitored over time and assigned a reputation score – good/bad/suspected. Imperva then applies different rules based on the client reputations and clients can set up custom access control rules for connecting clients based on this system.
At a high level, this is all accomplished by looking at several client attributes, including: Header data, IP and ASN verification, behavior monitoring, IP reputation (based on our own database as well as external sources) and client technology fingerprinting.
Architecturally, Imperva Account Takeover Protection is built on top of Imperva’s integrated single-stack architecture and deployed across a global network. This network includes a high-performance CDN that provides developer access to further protect against such a wide range of cybersecurity threats.
Built as part of our single-stack architecture, our detection and mitigation engines are inherent in-line capabilities of our cloud application security solution, and can benefit users of our cloud web application firewall (WAF). This purpose-built architecture allows us to immediately detect and mitigate risks at the edge without requiring any distant processing centers, utilizing crowdsourced community intelligence from our global network.
How Imperva Enlists AI/ML to Fight Account Takeover Attacks
Another aspect of Imperva Account Takeover Protection is its use of AI/ML to ensure that only business-critical traffic reaches websites by eliminating botnet traffic before it reaches a customer’s web apps. Imperva tracks emerging Account Takeover attack methods and incorporates them into its solution via machine learning. In addition, algorithms get continuously fine-tuned with this intelligence.
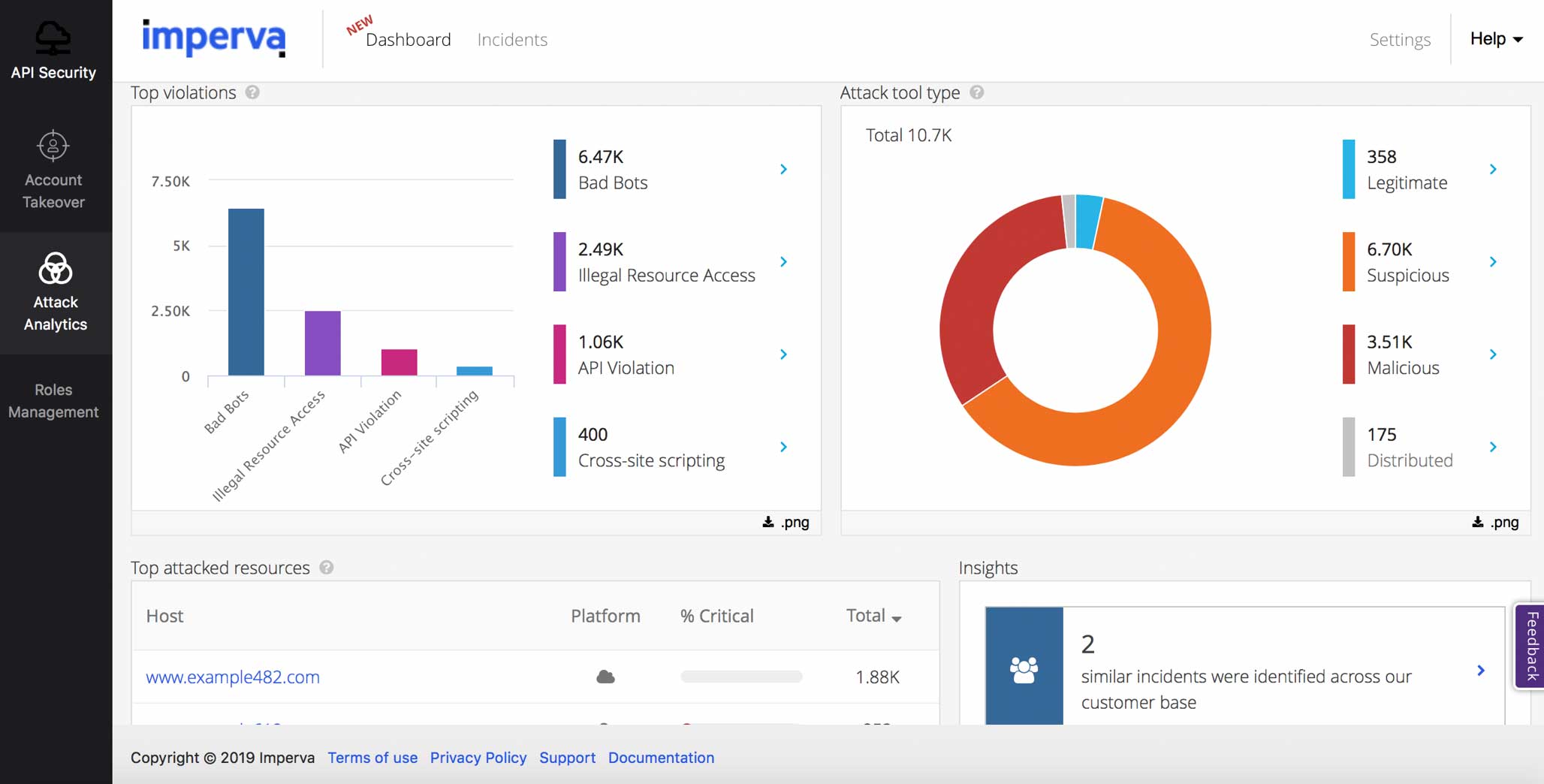
The idea is to make Imperva smart and proactive enough to ensure only business-critical traffic reaches websites, McGregor told IDN.
Imperva has a layered detection approach and uses a set of capabilities that help us differentiate between good and bad bots. The Imperva global network gives us a dynamic view that feeds our artificial intelligence models with detailed information all the time. We collect data on devices and IPs which are automatically added to our reputation engine. This updated knowledge is spread across our customer base, leading to fast and accurate detection.
We also utilize machine learning to generate a mitigation strategy per attack. The detection certainty of an account takeover attack depends on the accumulated information that we have on a specific entity at a given time.
When it comes to account takeover protection, we gather account takeover attempt data and this allows us to correlate between suspected login attempts and pinpoint credential stuffing attempts even when an attacker uses a fresh credential list. This intelligence combines with our multi-stage machine learning models and real-time information from our security research team to provide the ultimate level of protection.
We believe that providing early visibility into a potential attack is important, and that we should notify customers of any suspicious activity or any login that we identify has potential for an attack.
As a result, Imperva can provide ATO customers with situational capabilities, McGregor said. Among them:
To date, evidence shows that the cyber incident impacting Imperva’s Cloud WAF during the summer had no effect on ATO’s functionality or operations, McGregor said. He shared this statement with IDN.
While the incident is still under investigation, the incident impacted a subset of our customers who had accounts up to September 2017. . . The ATO functionality was launched in June 2019.
We have informed impacted customers directly and shared the steps we are taking to safeguard their accounts and data, and additional actions they can take themselves. We will provide more information as we know more.”
[Details on the security incident, and Imperva’s steps to mediate issues, were shared in a blog post from Imperva CEO Chris Hylen, which reads in part:]
We continue to investigate this incident around the clock and have stood up a global, cross-functional team. Here are the actions we have taken:
- We activated our internal data security response team and protocol and continue to investigate with the full capacity of our resources how this exposure occurred.
- We have informed the appropriate global regulatory agencies.
- We have engaged outside forensics experts.
- We implemented forced password rotations and 90-day expirations in our Cloud WAF product.
- We are informing all impacted customers directly and sharing the steps we are taking to safeguard their accounts and data, and additional actions they can take themselves.
Imperva ATO is Fending Off 70,000 Attempts Every 5 Minutes For A Single Customer
Since the ATO solution has gone live, McGregor said, it is performing strongly – and shared an example.
A customer site was “tagged as being under attack by all of our indicators,” McGregor told IDN. “Imperva noticed more than 50,000 unique IPs were used in this attack, from all around the globe. Most of the requests were classified as ‘Bot,’ but were declared as a legitimate browser, such as Firefox or Chrome,” he said.
“At its peak, there were almost 70,000 ATO attempts every 5 minutes – and zero user logins were compromised during that time,” he noted.
Perhaps most noteworthy. McGregor shared that this attack on the Imperva customer is still going on – and was not just a one-time assault.
“This attack is still ongoing, as the same IPs are being used over and over, possibly trying different ways/rates of attack.” So far, Imperva has mitigated over 5 million requests and counting. The customer has indicated that since mitigation was turned on, they have received no calls to helpdesk regarding the customer not being able to log in, meaning the false-positive rate is extremely low,” he said.
Imperva Account Takeover Protection is available now.
Related:
All rights reserved © 2025 Enterprise Integration News, Inc.


