Gravitational Updates Its Open Source Management To Deliver IoT-Centric Security
Gravitational is delivering IoT capability in the latest update to its popular open source access management solution, Teleport. Teleport 4.0 delivers IoT-centric security using modern privileged access management by letting developers leverage existing SSH-based toolchains.
Gravitational is delivering an Internet of Things (IoT) capability in the latest update to its popular open source access management solution, Teleport.
As part of Teleport 4.0, Gravitational’s solution will enable organizations to safely access IoT infrastructure by offering remote device management visibility and logging activity, according to Gravitational CEO Ev Kontsevoy. The new IoT-optimized access management solution was developed as a result of the high rate of vulnerability internet-connected devices can be exposed to, he added.
“It is all too common to see companies struggling to secure their IoT infrastructure. Teleport gives companies the single pane of glass they need to clearly see what is happening with their IoT devices and cloud servers,” Kontsevoy said in a statement.
Although most computer security professional work in data centers to manage security concerns, not all management tools, practices and expertise are capable of tackling problems associated with the vulnerability of IoT devices.
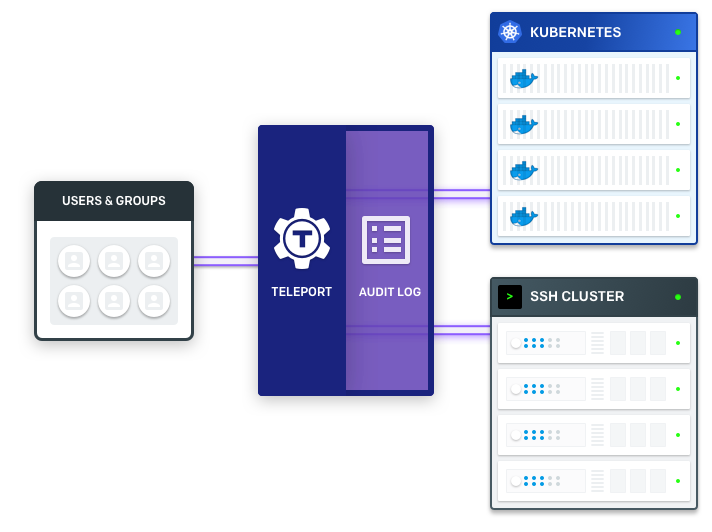
To fill the gap, Teleport 4.0 delivers IoT-centric security by letting IoT developers leverage existing SSH-based toolchains to push code updates and collect monitoring information from remote IoT devices. This approach improves security and allows for more direct enforcement of compliance, Kontsevoy said.
“Our goal is to empower our users to leverage their existing investments in SSH-based deployment tools or in Kubernetes to implement IoT security and compliance successfully and to lower the operational overhead of running code in both contexts,” he added.
Teleport Tackles Issues of IoT Security, Management
Although IoT manufacturers try to address potential vulnerabilities by eliminating the need for remote management, however, this isn’t feasible for remote devices that run on complex applications in industrial settings. These appliances have no direct network access to them, so using Teleport IoT is the only way to access them.
In a recent blog post, Gravitational’s Jon Silvers explained the technical issues – and Teleport’s fix – for delivering better IoT security.
Often the problem with securing and managing hundreds or thousands of remote IoT devices is that they don’t have public IP addresses and are hard to access.
With Teleport 4.0, nodes gain the ability to tunnel back to the main Teleport Proxy server and this outbound connection is used to bypass firewall restrictions and for access on the target infrastructure. With this feature, every lightweight Teleport node can dial back to the trusted Teleport cluster.
Teleport’s new IoT security features have a couple very important benefits including:
Streamlined logging: Instead of having to pull audit logs from each machine, Teleport centralizes operations to put them under one cluster, greatly simplifying reviewing past recordings and audit information.
Reduced operational overhead: Configuration and administration is all managed through a single Teleport cluster rather than through each device. Teleport’s RBAC features and integration with SAML and OIDC identity solutions means that admins no longer have to configure multiple cluster relationships and role mappings.
The problem associated with managing thousands of remote IoT is that they do not have public IP addresses and are difficult to access. However, with Teleport 4.0 IoT experts can bypass firewall restrictions, streamlined logging and reduced operational overhead.
Silvers also went on to describe Teleport’s added scalability
Teleport 4.0 offers significantly more scale. You can now connect to up to 10,000 remote connections to a single Teleport cluster for companies who need to support larger operations. While this feature was driven in part by the need to support thousands of IoT devices, it’s usable for any infrastructure security use case.
Teleport for IoT is being used in production by several of our customers, including TriNetX, a global health research network that optimizes clinical research, which is using the IoT features for managing their appliances in hospital settings. With Teleport, TriNetX can push software updates, collect monitoring data and keep audit logs across all of the remote devices, according to TriNetX’s director of engineering Konstantine Krutiy.
said of Teleport for IoT, “Teleport greatly streamlines the process of maintaining scores of devices while ensuring the data on the appliance is secure. With Teleport, we can clearly and securely see what is happening within our network of devices and have centralized logging and session recording, which helps us meet security and compliance.” Krutiy said in a statement.
Teleport Availability, Open Source & Commercial Options
Teleport 4.0 is available through the free, open-source community edition or commercial offerings.
It comes with a rich set of modern privileged access management capabilities, including: Multi-Factor Authentication (MFA); identity-based authentication; multi-cloud authentication, Kubernetes and SSH integration, along with security audit logging, role-based access controls and a host of other security, access and compliance features.







