Orkus Uses AI To Help Enterprises Protect Against Unauthorized Access To Cloud Resources, Infrastructure
Start-up firm Orkus is bringing AI to the task of protecting against unauthorized access to cloud resources and core infrastructure. The Orkus Access Governance Platform provides automated and continuous access governance for cloud across infrastructure, data and privileged identities.
Start-up firm Orkus is bringing AI to the task of protecting against unauthorized access to cloud resources and core infrastructure. The Orkus Access Governance Platform provides automated and continuous access governance for cloud across infrastructure, data and privileged identities.
“Enterprises are rapidly adopting cloud infrastructure for digital transformation initiatives, however one of the key risks holding them back is unauthorized access, because legacy methods of controlling access are not working,” said Orkus CEO and co-founder Manish Kalia in a statement. The Orkus Access Governance Platform is engineered to provide continuous and comprehensive access governance covering all three areas, Kalia added.
In specific, the Orkus Access Governance Platform was developed to prevent unauthorized access in cloud caused by several main factors:
- weak or ineffective access and authorization controls
- operator error
- insider threats
It’s no coincidence that these same three factors were cited as the top threats to cloud security in a recent Cybersecurity Insiders report.
To respond to these risks, Orkus enables organizations “to implement continuous governance of access and authorization for sensitive data, critical infrastructure and privileged identities,” Kalia noted.
To deliver these protections to cloud resources, the Orkus Access Governance Platform uses several key technologies, including artificial intelligence and machine learning. Specifically, Orkus has
Orkus Graph AI: Orkus uses Graph AI to learn “who” has access to “what” and “how” the access is being used. By applying machine learning on the access graph, Orkus understands access intent and usage across infrastructure, data, and identities in your cloud infrastructure. Orkus Graph AI detects risks such as unused or stale privileged access, data exposure, and insider threats.
Find Excess Privileges
Excess and unused privileges are one of the biggest security risks and it is rampant in all Enterprises. Orkus instantly identifies user and service accounts with excess or stale privileges that pose a risk to your cloud assets.
Identify High Risk Access
Orkus monitors in real time all changes in access for every object and identity in the cloud and identifies high risk access caused by malicious intent or operator errors.
Detect Access Abuse
Orkus continuously analyzes access usage patterns including type, volume, location, time and many other attributes to identify anomalous or suspicious access activity.
Orkus Access Intelligence: The Orkus Access Intelligence provides the ability to search, investigate and audit access and authorization, both currently and historically - across the cloud infrastructure.
Orkus also offers ways to leverage its AI capabilities to provide rich visibility features to deliver effective governance and risk mediation. Among them:
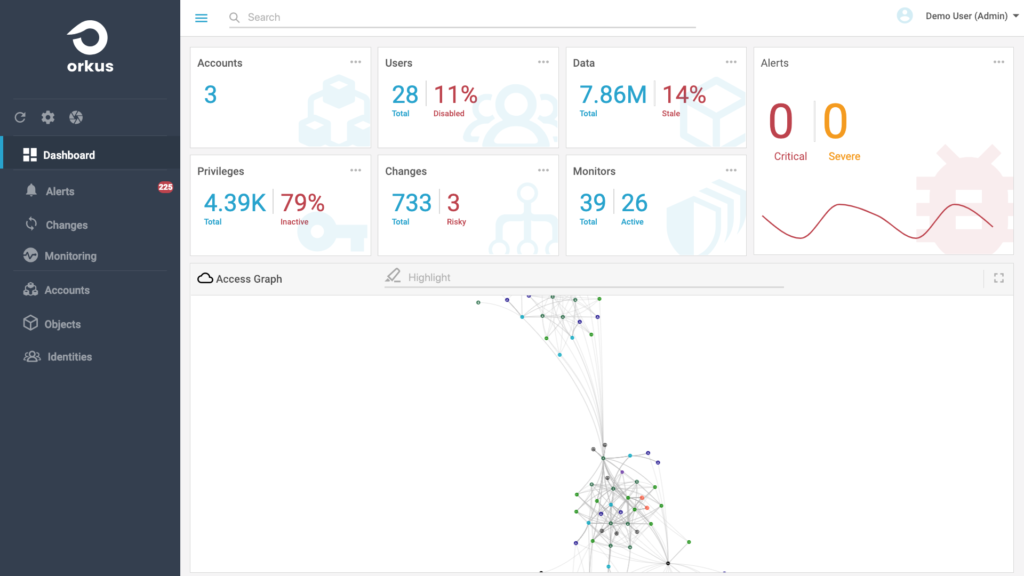
Orkus Access Graph: the Access Graph simplifies the task of governance by the building a real-time graph. This captures critical relationships between data, infrastructure, and identities that exist within an organization’s dynamic cloud infrastructure. The result: Orkus Access Graph automatically unifies silos of access and authorization across your hybrid cloud and provides simple, searchable and actionable intelligence.
Orkus Access Graph, which scales to work with millions of cloud objects, offers companies the ability to
Investigate Incidents
Investigate present and historical access with one simple query. Analyze access pattern changes and identify threats over a user-selectable period i.e. the last week, month, or year.
Automate Audit Reports
Easily create automated audit reports for privileged access and data access to prove to auditors your security controls.
Prioritize Certifications
Prioritize access certifications to focus on high-risk access, eliminate rubber stamping, and stop ineffective, time consuming manual processes.
Orkus Access Guardrails: Orkus automatically creates Guardrails to secure access to sensitive data and critical infrastructure and maintain compliance with mandates such as PCI, HIPAA, and GDPR. As such, these guardrails provide a key method for automating access governance in the cloud. With guardrails, security and compliance teams can specify access control intent -- without worrying about managing hundreds of low-level access and authorization policies.
Early feedback for Orkus’ approach to cloud governance has been positive. One notable customer, a former CISO at the CIA and now CEO 2BSecure Robert Bigman said in a statement:
“Throughout my entire career as a CISO, I've seen security teams struggle with access management, and not for lack of trying. The Orkus platform delivers automation to an area of security in grave need of it, empowering IT teams to secure access to their data, apps, and infrastructure. Orkus’s graph-based approach provides a quantum leap forward in managing access and authorization enterprise-wide.”






