Akamai Delivers Cloud-Based Security, Powered by Smart Algorithms, To Thwart DNS, Malware Attacks
Akamai Technologies, well known for high-performance content delivery over the Internet, is leveraging that knowledge to deliver a high-impact security service from the cloud. IDN talks with Akamai’s Frank Childs to learn how its Enterprise Threat Protector thwarts DNS, malware and bot attacks.
by Vance McCarthy
Tags: Akamai, analytics, cloud, DNS, malware, security,

senior director for product marketing
enterprise division

"Attackers are constantly finding new ways to launch threats at the DNS layer."
 Powering Digital Transformation with APIs, Cloud, IoT, Mobile & SOA
Powering Digital Transformation with APIs, Cloud, IoT, Mobile & SOAAkamai Technologies, well known for high-performance content delivery over the Internet, is leveraging that knowledge to deliver a high-impact security service from the cloud.
Akamai’s Enterprise Threat Protector (ETP) aims to protect against complex targeted threats such as malware, ransomware, phishing and DNS‑based data exfiltration, according to Frank Childs, senior director for product marketing at Akamai’s Enterprise Division.
The key to Akamai’s ETP is the company’s many years of expertise in DNS (Domain Name System or Domain Name Servers), which are the heartbeat of the Internet's equivalent of a phone book.
DNS maintains a directory of domain names and translates them to IP addresses which computers use access Internet locations. As it happens, DNS is also the phone book used by the vast majority of malware, bad bots and other nefarious traffic. In fact, a whopping 91.3% of known bad malware uses DNS, according to Cisco Systems’ 2016 Annual Security Report.
Childs gave IDN two main reasons DNS presents such an attractive target to would-be attackers:
- A majority of software and clients rely on DNS to communicate with one another
- DNS does not have built-in intelligence, so on its own DNS cannot determine if a domain being requested by a user is safe or malicious.
“DNS offers an easy-to-exploit gap to attackers, mostly because most software uses it and there’s little visibility into what is really going on [at that layer]” Childs said. “Most security solutions don’t inspect inside a DNS packet. Attacking bots or malware can put small payloads aboard and exfiltrate data.” And, perhaps worst of all, Childs said that for as little DNS inspection as there is, “attackers are constantly finding new ways to launch threats at the DNS layer.”
Akamai’s designed ETP so it can
- Identify and block access to those domains known to host sites that are used to deliver malware and ransomware, and/or known to be associated with phishing attacks.
- Identify DNS data exfiltration attacks where the DNS protocol is leveraged as a way to send sensitive data outside of the enterprise.
- Disrupt communications between devices within an enterprise that have already been infected with malware and the bad actors’ command and control (C2) servers. [C2 is a common, Internet-based mechanism to control malware once it has infected systems.]
- Prevent access to web content that falls outside an enterprise’s acceptable use policy (This is because DNS is such an effective control and enforcement point for enterprise security teams.)
- Prevent DNS-based data exfiltration. Prevent access to malicious malware and phishing domains and prevent and shutdown C2.
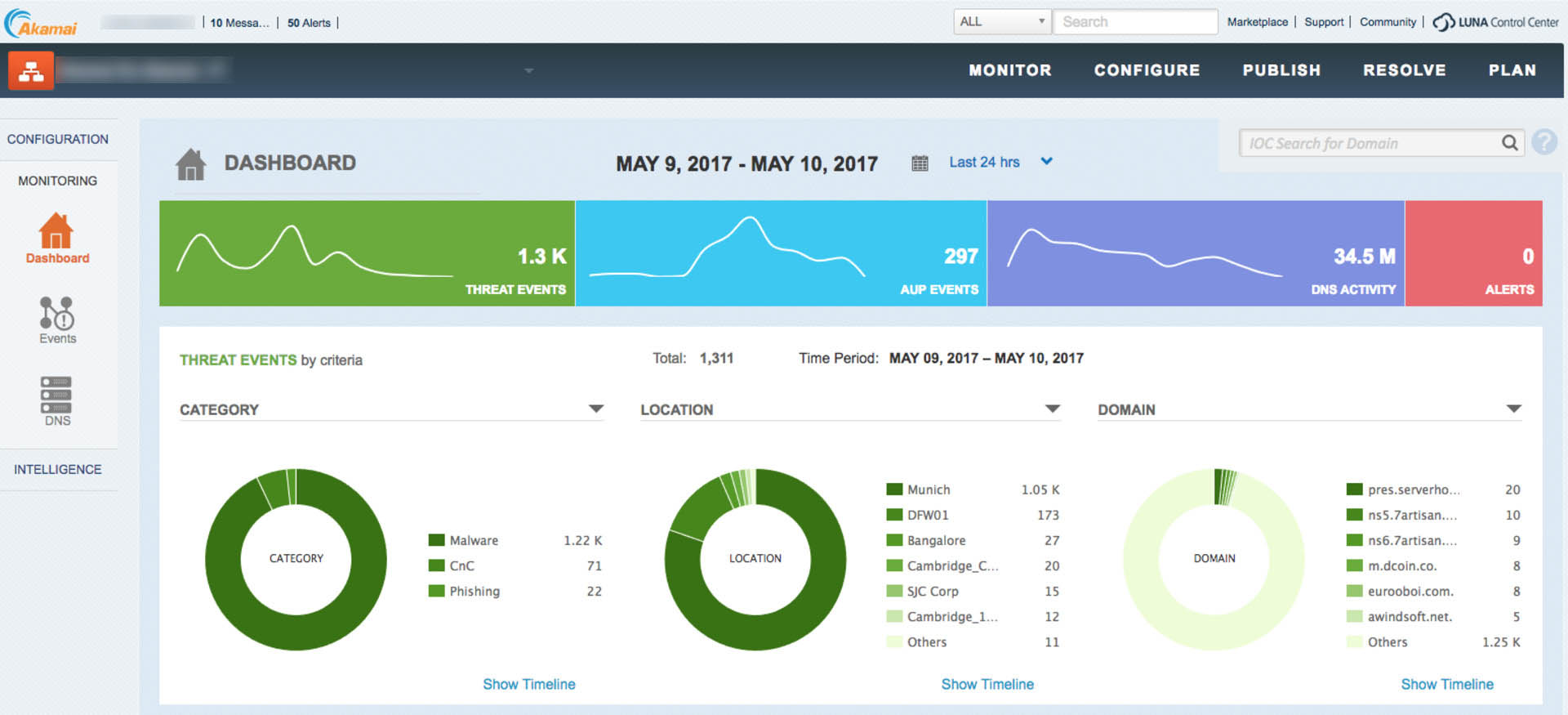
Interestingly, at the heart of Akamai’s approach is a simple fact. Much of today’s malware also relies on DNS, in this case to call to other systems or endpoints to inflict their damage. Shut down that communication and you can, in effect, neuter the attack. “No DNS. No Internet. So, for malware and other attacks it can often be ‘No communication. No attack,” Childs said.
For all its vulnerabilities, DNS also provides Akamai a made-to-order technique to find and shut down harmful traffic -- and even make it easy for companies to implement via a cloud-based service.
In specific, Akamai’s ETP approach uses a combination of its knowledge about how DNS works, along with a vast array of cloud-based metadata that reveals information to let Akamai distinguish good traffic from bad traffic that can cause harm.
“We’re bringing visibility and algorithms and fill an intelligence gap in DNS to help deliver an easy to deploy security solution,” Childs said. “DNS is such an elegant way to provide a layer of security without more boxes or upgrade boxes. And, because it’s available as a cloud service, a user can literally turn it on in 15 mins and see the impact.”
Akamai is, in essence, “creating cloud security intelligence at the DNS layer,” Childs told IDN. “It protects because based on our intelligence, it prevents all malware from phoning home, and prevents basically all C2 contacts [required for an attack].
DNS is a natural technique for Akamai to employ for security. The company has long years of experience using DNS for request routing, and is awash in DNS-centric data (that offers great clues to whether traffic may be good or harmful).
“On our network alone, we have 180 billion DNS requests a day go over our DNS systems. We then combine our data with data from third party feeds and we have a pretty good picture of what is chirping on the Internet,” Childs told IDN. To all that DNS chirping, Akamai applies a set of advanced – and always updated – algorithms, developed by the company’s threat intelligence team. These identify what traffic is safe or risky.
A technical blog post recently shared some details on how Akamai’s Cloud Security Intelligence capabilities gather and use this data – at mission-critical volumes and speeds:
Through the ability to analyze more than 20 Terabytes of daily web attack traffic associated with hundreds of millions of unique IP addresses on an hourly basis, the Akamai Cloud Security Intelligence is designed to provide more comprehensive insight into how malicious actors are attacking web properties, which in turn can be used to inform the direction of Akamai's Cloud Security Solutions.
Akamai’s ETP is architected to address vulnerabilities in DNS infrastructure that are emerging in the new era of exploding use of cloud native and hybrid IT solutions. Specific use case capabilities and features include:
Defend against (and close) DNS security gaps: Proactively blocks DNS requests to malware drop-sites, ransomware sites, malware command and control sites and DNS data exfiltration and phishing domains based on unique and up-to-date threat intelligence.
Cloud-driven scale: Avoids the use of hardware or on-prem software via a fully cloud‑based solution. This is designed to be configured and deployed in minutes with no disruption for users.
Reduced management: IT can manage security from anywhere and deploy policies in seconds to protect all locations.
Easily improve compliance: Companies can enforce their ‘acceptable use policy’ by blocking access to objectionable or inappropriate domains.
Childs concedes that DNS security will not be a single-point solution for securing the distributed, digital enterprise but DNS security will play a more crucial, and better understood role.
“Today users, devices, apps and data can be anywhere. So, there will be a huge disruption in what people think of as the DMZ,” Childs said. “So, at Akamai we’re looking at an ‘enterprise cloud perimeter’ that will bring more and more intelligence to security to secure access to everything – apps, data, devices and users.”
Childs says this need to think about and design security with an ‘enterprise cloud perimeter’ in mind will impact many long-relied upon security solutions, including SSO, Active Directory, identity management and multi-factor authentication. On that score, Akamai is partnering with Okta and plans other partnerships in the future.
“Enterprises can’t afford to spend significant time deploying and operationally scaling new security layers given the rate of change of the advanced threat landscape,” Childs said.
Related:
- Cloud Migration Isn’t Going Away: 4 Warning Signs a Change is Needed
- Qumulo Latest Driver Improves Storage Management of Kubernetes Apps and Workflows
- Cloudflare Unifies Email Security and Zero Trust with Acquisition of Area 1 Security
- 5 Ways Companies Can Protect Themselves When AWS Goes Down
- Astadia Joins the AWS Mainframe Modernization Service
All rights reserved © 2025 Enterprise Integration News, Inc.


